 固态硬盘安全功能在国防当中的应用
固态硬盘安全功能在国防当中的应用
Security Features for Solid State Drives in Defense Applications
译文简介
翻译了有关固态硬盘在军用上的资料白皮书其中的一部分
正文翻译
There are various methods for data protection and elimination in Flash solid state drives (SSDs),depending on the security level required within each application. Security techniques can be divided into three categories:
固态硬盘(SSD)数据保护和销毁方式多种多样,具体则取决于每种应用的所需的安全等级。 安全技术可以被分为三类:
固态硬盘(SSD)数据保护和销毁方式多种多样,具体则取决于每种应用的所需的安全等级。 安全技术可以被分为三类:
1. Data protection
2. Data elimination
3. Media destruction
1.数据保护
2.数据销毁
3.媒介破坏
2. Data elimination
3. Media destruction
1.数据保护
2.数据销毁
3.媒介破坏
Methods of data protection include write protection, password protection and encryption. Password protection can be used in combination with a biometric key to implement a security scheme that is based on “what you have, what you know, who you are”.
数据保护方法包括写入保护,密码保护和加密。密码保护可与生物识别密钥结合使用,以实现基于 "你拥有什么、你知道什么、你是谁 "的安全方案。
数据保护方法包括写入保护,密码保护和加密。密码保护可与生物识别密钥结合使用,以实现基于 "你拥有什么、你知道什么、你是谁 "的安全方案。
Data elimination is handled by Clear and Sanitize procedures. Which method needs to be implemented depends on the security classification level of the organization in which the application resides.
数据销毁由清除(完全擦除数据)和消毒(去除敏感信息但同时保留数据其它有用部分)程序处理。采用哪种方法取决于应用程序所在组织的安全分类级别。
数据销毁由清除(完全擦除数据)和消毒(去除敏感信息但同时保留数据其它有用部分)程序处理。采用哪种方法取决于应用程序所在组织的安全分类级别。
Typically, if the device will stay within the same security classification, a Clear procedure will suffice.If it is moved to a higher security classification level, the device needs to be entirely declassified, and a Sanitize procedure is needed. Moving the device to a lower security classification would require destruction of the drive.
通常情况下,设备如果保持在同一安全等级内,则只需执行 "清除 "程序即可。如果将设备移至更高的安全等级,则需要对设备进行完全解密,并执行 "消毒 "程序。如果将设备移动到较低的安全分类级别,则需要销毁硬盘。
通常情况下,设备如果保持在同一安全等级内,则只需执行 "清除 "程序即可。如果将设备移至更高的安全等级,则需要对设备进行完全解密,并执行 "消毒 "程序。如果将设备移动到较低的安全分类级别,则需要销毁硬盘。
Sanitizing a solid state drive is much faster and requires fewer cycles of the same procedure when compared to hard disk drives, since SSDs experience far lower levels of data remanence.
与硬盘驱动器相比,固态硬盘的消毒速度更快,所需的相同程序循环次数也更少,因为固态硬盘的数据残留水平要低得多。
与硬盘驱动器相比,固态硬盘的消毒速度更快,所需的相同程序循环次数也更少,因为固态硬盘的数据残留水平要低得多。
Complete media destruction can be a solution if a Sanitize procedure is too time consuming. However,incineration or disintegration can be expensive and impractical for many situations.
如果消毒程序过于耗时,完全销毁介质也是一种解决方案。不过,焚化或分解可能会很昂贵,而且在很多情况下不切实际。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
如果消毒程序过于耗时,完全销毁介质也是一种解决方案。不过,焚化或分解可能会很昂贵,而且在很多情况下不切实际。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
In April 2001, a US Navy surveillance plane was intercepted by two Chinese F-8 fighter planes during a routine patrol flight over the Chinese South Sea.The US plane was forced to make an emergency landing in China, after what officials described as a “minor” midair collision, occured with one of the Chinese planes.
2001 年 4 月,一架美国海军侦察机在中国南海上空进行例行巡逻飞行时,遭到两架中国 F-8 战斗机的拦截。在与其中一架中国飞机发生了被官方称为 "轻微 "的空中碰撞后,美国飞机被迫在中国紧急迫降。
2001 年 4 月,一架美国海军侦察机在中国南海上空进行例行巡逻飞行时,遭到两架中国 F-8 战斗机的拦截。在与其中一架中国飞机发生了被官方称为 "轻微 "的空中碰撞后,美国飞机被迫在中国紧急迫降。
The US crew had between 12 and 20 minutes in the air to destroy all classified material on board before making the emergency landing. In the final moments before the plane landed, the crew tried to destroy the
hardware with hammers and axes. Just how much the crew was able to destroy is not public knowledge.
美国机组人员在空中有 12 至 20 分钟的时间销毁机上所有机密材料,然后紧急迫降。在飞机着陆前的最后时刻,机组人员试图用锤子和斧头销毁硬件。至于机组人员能够销毁多少,公众并不知晓。
hardware with hammers and axes. Just how much the crew was able to destroy is not public knowledge.
美国机组人员在空中有 12 至 20 分钟的时间销毁机上所有机密材料,然后紧急迫降。在飞机着陆前的最后时刻,机组人员试图用锤子和斧头销毁硬件。至于机组人员能够销毁多少,公众并不知晓。

This story illustrates the need for high-level security methods in defense systems, and in particular for the storage devices within these systems. This story is at the far end of the security spectrum; there are many systems that require lesser forms of security. For example, devices such as data recorders and ruggedized laptops that are used in training environments require a lower security implementation.
这个故事说明了防御系统中高级安全解决方法的必要性,特别是这些系统内部的存储设备。这个故事处于安全范围的最高端;还有许多系统需要较低形式的安全保障。例如,在培训环境中使用的数据记录器和强化笔记本等设备需要较低级别的安全实施。
Since these devices stay within the same security classification environment, fast elimination of mission data may be all that is required once a training mission has been completed. On the other hand, if the device is moved to an environment with a higher security classification, a complete Sanitize procedure per the specified defense department standard will be required. Moving the device to an environment with a lower security classification requires complete destruction of the device.
由于这些设备仍处于同一安全分类环境中,因此一旦完成培训任务,只需快速消除任务数据即可。另一方面,如果将设备转移到安全等级更高的环境中,则需要按照指定的国防部标准执行完整的 "消毒 "程序。将设备转移到安全等级较低的环境中,则需要彻底销毁设备。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
由于这些设备仍处于同一安全分类环境中,因此一旦完成培训任务,只需快速消除任务数据即可。另一方面,如果将设备转移到安全等级更高的环境中,则需要按照指定的国防部标准执行完整的 "消毒 "程序。将设备转移到安全等级较低的环境中,则需要彻底销毁设备。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
In general, defense storage system security levels are divided into three categories:
通常国防存储系统安全等级主要分为三大类:
通常国防存储系统安全等级主要分为三大类:
1.Data protection
数据保护
数据保护
2.Data elimination
数据清除
数据清除
3.Media destruction
媒介销毁
媒介销毁
The third method would have definitely been preferred in the case of the US surveillance plane, but, of course, it is impractical, if not impossible, to have incineration or disintegration equipment inside an aircraft.
就上述美国侦察机而言,第三种方法肯定是首选,但是,在飞机内安装焚烧或分解设备是不切实际,甚至是不可能的。
就上述美国侦察机而言,第三种方法肯定是首选,但是,在飞机内安装焚烧或分解设备是不切实际,甚至是不可能的。
SMART High Reliability Solutions (SMART HRS) designs and develops security functionality in accordance with commonly used military specifications. As a result of this focus, SMART HRS solid state drives find wide acceptance and deployment in defense applications.
智能高可靠性解决方案 (SMART HRS) 根据常用的军用规范设计和开发的安全功能。由于专注于此,SMART HRS 的固态硬盘在国防应用中得到了广泛的认可和部署。
智能高可靠性解决方案 (SMART HRS) 根据常用的军用规范设计和开发的安全功能。由于专注于此,SMART HRS 的固态硬盘在国防应用中得到了广泛的认可和部署。
This white paper discusses the various solid state drive data security methods that can be applied in defense applications and environments, and discusses Secure Data Elimination Technology (SDET) implemented within the solid state drive product line from SMART HRS.
本白皮书讨论了可应用于国防应用和环境的各种固态硬盘数据安全方法,并讨论了 SMART HRS 在固态硬盘产品线中实施的安全数据消除技术 (SDET)。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
本白皮书讨论了可应用于国防应用和环境的各种固态硬盘数据安全方法,并讨论了 SMART HRS 在固态硬盘产品线中实施的安全数据消除技术 (SDET)。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
4.SECURITY IN SOLID STATE DRIVES VS. HARD DISK DRIVES
在安全领域固态硬盘VS. 机械硬盘
在安全领域固态硬盘VS. 机械硬盘
Implementing security features that require data elimination or media destruction is far more complex for hard disk drives than solid state drives due to their underlying storage technology. For example, hard disk drives leave behind a much bigger “ghost-image” once data is written to them. This requires more complex and longer data elimination procedures than would be needed for solid state drives.
对于机械硬盘来说,由于其基础存储技术,实施消除数据或销毁介质的安全功能要比固态驱动器复杂得多。例如,数据写入硬盘后,硬盘会留下更大的 "重影"。这就需要比固态硬盘更复杂、更长的数据消除程序。
对于机械硬盘来说,由于其基础存储技术,实施消除数据或销毁介质的安全功能要比固态驱动器复杂得多。例如,数据写入硬盘后,硬盘会留下更大的 "重影"。这就需要比固态硬盘更复杂、更长的数据消除程序。
In general, the amount of data that could possibly remain after a simple erase on a particular storage medium dictates the complexity of the data elimination and media destruction techniques on that storage medium. The smaller the data remanence on the storage media, the more simple data elimination techniques can be implemented. The next sections review data remanence on hard disk drives and solid state drives.
一般来说,特定存储介质上经过简单擦除后可能残留的数据量决定了该存储介质上数据消除和介质销毁技术的复杂程度。存储介质上的数据残留量越小,采用的数据消除技术就越简单。接下来的章节将回顾硬盘驱动器和固态驱动器上的数据残留情况。
一般来说,特定存储介质上经过简单擦除后可能残留的数据量决定了该存储介质上数据消除和介质销毁技术的复杂程度。存储介质上的数据残留量越小,采用的数据消除技术就越简单。接下来的章节将回顾硬盘驱动器和固态驱动器上的数据残留情况。
3.1Data Remanence in Hard Disk Drives
机械硬盘中的数据残留
机械硬盘中的数据残留
When data is written to a magnetic medium, the write head sets the polarity of most, but not all, of the magnetic substrate. This is partially due to the inability of the write head to write in exactly the same location each time, and partially due to the variations in media sensitivity and field strength among devices over time.
当数据写入磁性介质时,写磁头会设置大部分磁性基板的极性,但不是全部。部分原因是写磁头无法每次都在完全相同的位置写入,部分原因是随着时间的推移,设备之间的介质灵敏度和磁场强度会发生变化。
当数据写入磁性介质时,写磁头会设置大部分磁性基板的极性,但不是全部。部分原因是写磁头无法每次都在完全相同的位置写入,部分原因是随着时间的推移,设备之间的介质灵敏度和磁场强度会发生变化。
When a “1” is written to a disk, the media records a ”1”. When a “0” is written, the media records a ”0”. However, the actual effect is closer to obtaining a 0.95 when a “0” is overwritten with a “1” and a 1.05 when a “1” is overwritten with a ”1”. Deviations of the drive head from the original track may leave significant portions of the previous data along the track edge. Normal disk circuitry is set up so that both these values are read as ”1”, but using specialized tools such as a magnetic force microscope, it is possible to read what previous layers contained. Using thesebspecialized tools, extracting so-called “ghost-images” becomes fairly easy.
当向磁盘写入“1”时,介质记录为“1”。当写入“0”时,介质记录为“0”。然而,实际效果更接近于当“0”被覆盖为“1”时获得0.95,当“1”被覆盖为“1”时获得1.05。磁头从原始轨道偏离可能会使轨道边缘保留大部分先前的数据。普通磁盘电路设置为将这两个值都读取为“1”,但是使用专门的工具,比如磁力显微镜,可以读取以前的层次包含的内容。使用这些专门的工具,提取所谓的“幽灵图像”变得相当容易。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
当向磁盘写入“1”时,介质记录为“1”。当写入“0”时,介质记录为“0”。然而,实际效果更接近于当“0”被覆盖为“1”时获得0.95,当“1”被覆盖为“1”时获得1.05。磁头从原始轨道偏离可能会使轨道边缘保留大部分先前的数据。普通磁盘电路设置为将这两个值都读取为“1”,但是使用专门的工具,比如磁力显微镜,可以读取以前的层次包含的内容。使用这些专门的工具,提取所谓的“幽灵图像”变得相当容易。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
To ensure a complete elimination of a “ghost-image”on a magnetic disk drive, two procedures can be followed:
要确保完全消除磁盘驱动器上的 "鬼影",可以遵循两个程序:
要确保完全消除磁盘驱动器上的 "鬼影",可以遵循两个程序:
· Degaussing the media by applying a reverse (coercive) magnetizing force in order to reduce the correlation between previous and present data to a point that there is no known technique for recovery of previous data.
通过施加反向(强制)磁化力对介质进行消磁,以降低先前数据和当前数据之间的相关性,以至于没有已知的技术来恢复先前的数据。
通过施加反向(强制)磁化力对介质进行消磁,以降低先前数据和当前数据之间的相关性,以至于没有已知的技术来恢复先前的数据。
· Overwriting the media multiple times with various patterns. A one-time erase of the media will not suffice and military standards specify up to four Sanitize cycles of erase and pattern-overwrite. However, according to industry recommendations, a pattern overwrite of up to 35 times is required to completely clear previously contained data from the media.
用各种模式多次覆写介质。一次性擦除介质是不够的,军用标准规定最多可进行四次 "消毒 "循环擦除和模式覆写。不过,根据行业建议,要彻底清除介质中以前包含的数据,需要进行多达 35 次的模式覆写。
用各种模式多次覆写介质。一次性擦除介质是不够的,军用标准规定最多可进行四次 "消毒 "循环擦除和模式覆写。不过,根据行业建议,要彻底清除介质中以前包含的数据,需要进行多达 35 次的模式覆写。
3.2Data Remanence in Solid State Drives
固态硬盘中的数据残留
固态硬盘中的数据残留
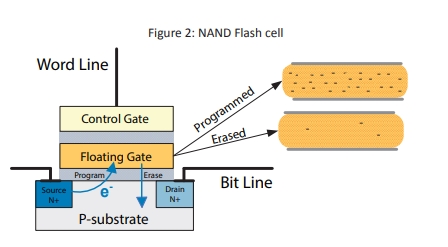
Solid state drives use NAND Flash technology for data storage. Figure 2 below shows the internal structure of a NAND Flash cell, which uses a process known as Fowler-Nordheim tunneling to change the charge inside the floating gate.
固态硬盘使用 NAND 闪存技术存储数据。下图 2 显示了 NAND 闪存单元的内部结构,它使用一种称为 Fowler-Nordheim 隧道技术的工艺来改变浮动栅极内的电荷。
固态硬盘使用 NAND 闪存技术存储数据。下图 2 显示了 NAND 闪存单元的内部结构,它使用一种称为 Fowler-Nordheim 隧道技术的工艺来改变浮动栅极内的电荷。
Writing (programming) a “0” into a cell causes the accumulation of negative charges in the floating gate. Writing a “1” into a cell does not change the cell’s content. To change the content of a cell from “0” to “1”, the cell must be erased in order to release the negative charges in the floating gate.
向单元写入(编程)"0 "会导致浮动栅负电荷累积。向单元写入 "1 "不会改变单元的内容。要将单元内容从 "0 "改为 "1",必须擦除单元,以释放浮动栅极中的负电荷。
向单元写入(编程)"0 "会导致浮动栅负电荷累积。向单元写入 "1 "不会改变单元的内容。要将单元内容从 "0 "改为 "1",必须擦除单元,以释放浮动栅极中的负电荷。
Data remanence in NAND Flash is mainly caused by a so-called hot-carrier effect, where electrons get trapped in the gate oxide layer and can stay there as excess charge. The amount of trapped charge can be determined by measuring the gate-induced drain leakage current of the cell, or more indirectly by measuring the threshold voltage of the cell. The effect is more apparent in fresh cells, and becomes less noticeable after 10 program/erase cycles.
NAND 闪存中的数据残留主要是由所谓的热载流子效应造成的,即电子被困在栅极氧化层中,并作为过剩电荷留在那里。滞留电荷的数量可通过测量电池的栅极漏电流或更间接地测量电池的阈值电压来确定。这种效应在新电池中更为明显,10 次编程/擦除循环后就不那么明显了。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
Erasing the cell will significantly reduce the amount of trapped electrons, making it extremely difficult to recover any data from the device after an erase cycle.
擦除电池会大大减少滞留电子的数量,使得在擦除周期后极难从设备中恢复任何数据。
擦除电池会大大减少滞留电子的数量,使得在擦除周期后极难从设备中恢复任何数据。
3.3Flash SSD Data Abstraction Layers
An additional complexity to recovering data from a solid state drive (when compared to hard disk drives) arises from the fact that solid state drives contain additional data abstraction layers. In-depth knowledge would be required of the following layers to obtain a valid picture of the extracted data:
闪存固态硬盘数据抽象层
与硬盘相比,从固态硬盘恢复数据的额外复杂性来自于固态硬盘包含额外的数据抽象层。要获得提取数据的有效图像,需要深入了解以下各层:
An additional complexity to recovering data from a solid state drive (when compared to hard disk drives) arises from the fact that solid state drives contain additional data abstraction layers. In-depth knowledge would be required of the following layers to obtain a valid picture of the extracted data:
闪存固态硬盘数据抽象层
与硬盘相比,从固态硬盘恢复数据的额外复杂性来自于固态硬盘包含额外的数据抽象层。要获得提取数据的有效图像,需要深入了解以下各层:
· File system: Each file system has its own method of mapping files, creating pointers, and storing tables. Knowledge of this would be required for both HDD and solid state drives when data is extracted.
文件系统: 每个文件系统都有自己的映射文件、创建指针和存储表的方法。提取数据时,硬盘和固态硬盘都需要这方面的知识。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
文件系统: 每个文件系统都有自己的映射文件、创建指针和存储表的方法。提取数据时,硬盘和固态硬盘都需要这方面的知识。
原创翻译:龙腾网 https://www.ltaaa.cn 转载请注明出处
· Logical to physical mapping: Flash Management Systems map the logical file system sectors to physical locations on the Flash. Each solid state drive vendor implements a different Flash management algorithm for mapping sectors.
逻辑到物理映射: 闪存管理系统将逻辑文件系统扇区映射到闪存上的物理位置。每个固态硬盘供应商都采用不同的闪存管理算法来映射扇区。
逻辑到物理映射: 闪存管理系统将逻辑文件系统扇区映射到闪存上的物理位置。每个固态硬盘供应商都采用不同的闪存管理算法来映射扇区。
Solid state drive architecture: Each solid state drive vendor has a different architecture, and therefore it is hard to determine where in each Flash chip a logical block address ends up.
固态硬盘架构: 每个固态硬盘供应商都有不同的架构,因此很难确定逻辑块地址在每个闪存芯片中的最终位置。
固态硬盘架构: 每个固态硬盘供应商都有不同的架构,因此很难确定逻辑块地址在每个闪存芯片中的最终位置。
· Flash cell architecture: Different Flash vendors have different Flash cell architectures with different sequences of discrete bits.
闪存单元结构: 不同的闪存供应商有不同的闪存单元结构,其离散位序列也各不相同。
闪存单元结构: 不同的闪存供应商有不同的闪存单元结构,其离散位序列也各不相同。
The additional data abstraction layers in a solid state drive increase the complexity of reverse engineering,making it extremely difficult to extract sensible data.
固态硬盘中额外的数据抽象层增加了逆向工程的复杂性,使得提取合理数据变得极为困难。
固态硬盘中额外的数据抽象层增加了逆向工程的复杂性,使得提取合理数据变得极为困难。
DATA PROTECTION
数据保护
数据保护
At the most basic level of data security, hardware and software applications achieve protection from viruses or hackers through write protection and password access protection. These isolate the Operating System (OS), applications, and critical data from corruption or infiltration by external sources. Write and password protecting a drive can be meaningful in applications
where the end user is not allowed to tamper with the contents of the data.
在最基础的数据安全级别,硬件和软件的应用程序通过写入保护和密码访问保护来实现对病毒或黑客的防护。这些措施可隔离操作系统(OS)、应用程序和关键数据,使其免受外部资源的破坏或渗透。写入保护和密码保护硬盘在以下应用中意义重大在不允许最终用户篡改数据内容的应用中,写入保护和密码保护硬盘非常重要。
where the end user is not allowed to tamper with the contents of the data.
在最基础的数据安全级别,硬件和软件的应用程序通过写入保护和密码访问保护来实现对病毒或黑客的防护。这些措施可隔离操作系统(OS)、应用程序和关键数据,使其免受外部资源的破坏或渗透。写入保护和密码保护硬盘在以下应用中意义重大在不允许最终用户篡改数据内容的应用中,写入保护和密码保护硬盘非常重要。
4.1 Hardware Write Protection
Write protection prevents data modification on a storage device. It is typically enforced by the hardware through a jumper or switch and implemented through a hardware protection mechanism inside the controller of the SSD. In this case, a protection state machine inside the controller blocks writes to the media.
硬件写入保护
写入保护可防止存储设备上的数据被修改。它通常由硬件通过跳线或开关来执行,并通过固态硬盘控制器内部的硬件保护机制来实现。在这种情况下,控制器内部的保护状态机会阻止对介质的写入。
Write protection prevents data modification on a storage device. It is typically enforced by the hardware through a jumper or switch and implemented through a hardware protection mechanism inside the controller of the SSD. In this case, a protection state machine inside the controller blocks writes to the media.
硬件写入保护
写入保护可防止存储设备上的数据被修改。它通常由硬件通过跳线或开关来执行,并通过固态硬盘控制器内部的硬件保护机制来实现。在这种情况下,控制器内部的保护状态机会阻止对介质的写入。
4.2 Software Write Protection
Software write protection can be implemented through the firmware of the storage device, whereby the host can set or remove the write protection via a host (vendor-unique) command to the drive. Software password protection is suitable when implementing a security scheme that is based on “what you have, what you know, who you are” . For example, when only authorized personnel are allowed to download mission data from a data recorder, a combined password protection and biometric key would provide a secure identification scheme. In this case, the password would deliver the “what you know,” and a biometric key would cover the “what you have” and “who you are.”
软件写入保护
软件写入保护可以通过存储设备的固件实现,从而使主机可以通过主机(供应商特有)命令对驱动器设置或取消写保护。软件密码保护在执行安全计划时基于 "你有什么、你知道什么、你是谁 "的安全方案。例如,当只有授权人员才能从数据记录器中下载任务数据时,密码保护和生物识别密钥相结合就能提供一个安全的识别方案。在这种情况下,密码将提供 "你知道什么",而生物识别密钥将涵盖 "你是谁"。
Software write protection can be implemented through the firmware of the storage device, whereby the host can set or remove the write protection via a host (vendor-unique) command to the drive. Software password protection is suitable when implementing a security scheme that is based on “what you have, what you know, who you are” . For example, when only authorized personnel are allowed to download mission data from a data recorder, a combined password protection and biometric key would provide a secure identification scheme. In this case, the password would deliver the “what you know,” and a biometric key would cover the “what you have” and “who you are.”
软件写入保护
软件写入保护可以通过存储设备的固件实现,从而使主机可以通过主机(供应商特有)命令对驱动器设置或取消写保护。软件密码保护在执行安全计划时基于 "你有什么、你知道什么、你是谁 "的安全方案。例如,当只有授权人员才能从数据记录器中下载任务数据时,密码保护和生物识别密钥相结合就能提供一个安全的识别方案。在这种情况下,密码将提供 "你知道什么",而生物识别密钥将涵盖 "你是谁"。
4.2.1 Password Protection in SMART HRS Solid State Drives
The password protection feature on SMART HRS solid state drives is implemented through the standard ATA command set and supports both a user and master password. When used for data logging purposes, the device can be locked or unlocked at boot time when used as the boot device, or once an application is loaded.
SMART HRS 固态硬盘中的密码保护
SMART HRS 固态硬盘的密码保护功能通过标准 ATA 命令集实现,支持用户密码和主密码。当用于数据记录目的时,设备可在启动时作为启动设备锁定或解锁,或在加载应用程序后锁定或解锁。
The password protection feature on SMART HRS solid state drives is implemented through the standard ATA command set and supports both a user and master password. When used for data logging purposes, the device can be locked or unlocked at boot time when used as the boot device, or once an application is loaded.
SMART HRS 固态硬盘中的密码保护
SMART HRS 固态硬盘的密码保护功能通过标准 ATA 命令集实现,支持用户密码和主密码。当用于数据记录目的时,设备可在启动时作为启动设备锁定或解锁,或在加载应用程序后锁定或解锁。
· Password protection during boot: When the SMART HRS solid state drive is used as the boot
device, password protection is implemented in combination with the BIOS of the host system. The BIOS will need to incorporate the ATA commands that enable the usage of the password scheme. During the system boot process, the user must successfully enter a password to the system; otherwise the system will not continue booting.
启动过程中的密码保护 将 SMART HRS 固态硬盘用作启动设备时,密码保护将与主机系统的 BIOS 一起执行。BIOS 需要包含启用密码方案的 ATA 命令。在系统启动过程中,用户必须成功输入系统密码,否则系统将无法继续启动。
device, password protection is implemented in combination with the BIOS of the host system. The BIOS will need to incorporate the ATA commands that enable the usage of the password scheme. During the system boot process, the user must successfully enter a password to the system; otherwise the system will not continue booting.
启动过程中的密码保护 将 SMART HRS 固态硬盘用作启动设备时,密码保护将与主机系统的 BIOS 一起执行。BIOS 需要包含启用密码方案的 ATA 命令。在系统启动过程中,用户必须成功输入系统密码,否则系统将无法继续启动。
After five unsuccessful attempts of entering a password, the drive will have to be rebooted before new attempts can be made. These include both user and master password attempts.
在尝试输入密码五次之后,硬盘必须重启后才能进行新的尝试。这些包括用户密码和主密码尝试。
在尝试输入密码五次之后,硬盘必须重启后才能进行新的尝试。这些包括用户密码和主密码尝试。
4.3 Encryption
Another form of data protection is encryption, whereby the original data, or plaintext, is converted into a coded equivalent called ciphertext via an encryption algorithm. The ciphertext is decoded (decrypted) at the receiving end and turned back into plaintext.
加密
数据保护的另一种形式是加密,即通过加密算法将原始数据或明文转换成同等的加密编码,称为密文。密文在接收端被解码(解密),并变回明文。
Another form of data protection is encryption, whereby the original data, or plaintext, is converted into a coded equivalent called ciphertext via an encryption algorithm. The ciphertext is decoded (decrypted) at the receiving end and turned back into plaintext.
加密
数据保护的另一种形式是加密,即通过加密算法将原始数据或明文转换成同等的加密编码,称为密文。密文在接收端被解码(解密),并变回明文。
When using the most common encryption algorithms, such as RSA, AES and 3DES, it is virtually impossible to recover any data from a storage device,providing a high form of security. For example, to break an AES 128-bit encryption, a “bruteforce” attack with a system that tries keys at the rate of one billion keys per second will take about 10,000,000,000,000,000,000,000 years to try all possible keys.
在使用最常见的加密算法(如 RSA、AES 和 3DES)时,几乎不可能从存储设备中恢复任何数据。因此具有很高的安全性。例如,要破解 AES 128 位加密,如果系统以每秒 10 亿个密钥的速度尝试所有可能的密钥,那么 "暴力 "攻击将需要 10,000,000,000,000,000 年的时间。
在使用最常见的加密算法(如 RSA、AES 和 3DES)时,几乎不可能从存储设备中恢复任何数据。因此具有很高的安全性。例如,要破解 AES 128 位加密,如果系统以每秒 10 亿个密钥的速度尝试所有可能的密钥,那么 "暴力 "攻击将需要 10,000,000,000,000,000 年的时间。
The main hurdle that has prevented encryption from being integrated full scale into host applications and storage devices is related to key management. Creating strong and secure keys appears to be surprisingly difficult. The challenge is that most systems are notoriously deterministic, but what is required of a good and strong key is the opposite – unpredictability and randomness. In addition, it is not a trivial matter to provide a secure method of key storage and distribution without running the risk of keys being tampered with or stolen.
导致加密未能完全整合到主机应用程序和存储设备中的主要障碍与密钥管理有关。创建强大和安全的密钥似乎是难以逾越的困难。挑战在于大多数系统通常是确定性的,但一个好的、强大的密钥所需要的是相反的 - 不可预测性和随机性。此外,提供一种安全的密钥存储和分发方法并不是一件简单的事情,因为存在密钥被篡改或被盗的风险。
导致加密未能完全整合到主机应用程序和存储设备中的主要障碍与密钥管理有关。创建强大和安全的密钥似乎是难以逾越的困难。挑战在于大多数系统通常是确定性的,但一个好的、强大的密钥所需要的是相反的 - 不可预测性和随机性。此外,提供一种安全的密钥存储和分发方法并不是一件简单的事情,因为存在密钥被篡改或被盗的风险。
Most modern SSDs incorporate some form of encryption on the data they write to the NAND Flash. Since the SSD internally manages all the elements of the encryption from the key generation, to the key storage, to key deletion, they are called Self-Encrypting Drives (SEDs). In itself, an SED does not offer much data protection except deleting the encryption key in milliseconds, but when combined with other data protection features such as passwords, it provides an additional layer of data protection.
大多数现代固态硬盘都对写入 NAND 闪存的数据进行了某种形式的加密。由于固态硬盘内部管理着从密钥生成、密钥存储到密钥删除的所有加密要素,因此被称为自加密硬盘(SED)。SED 本身除了能在几毫秒内删除加密密钥外,并不能提供多少数据保护,但如果与密码等其他数据保护功能结合使用,就能提供额外的数据保护。
大多数现代固态硬盘都对写入 NAND 闪存的数据进行了某种形式的加密。由于固态硬盘内部管理着从密钥生成、密钥存储到密钥删除的所有加密要素,因此被称为自加密硬盘(SED)。SED 本身除了能在几毫秒内删除加密密钥外,并不能提供多少数据保护,但如果与密码等其他数据保护功能结合使用,就能提供额外的数据保护。
评论翻译
无
很赞 ( 1 )
收藏